5 useful pieces of information from the VeeamON 2019 global event

The end of May has found part of the ECKO team at VeeamON 2019 in Florida, the annual event organised by Veeam, together with the most relevant global partners. Why a 5000 km and 12 hour flight in the age of videoconferences? Because we like being wherever people talk about technology, because several product releases were announced, and because we could not miss the chance to meet with the Veeam specialists, as well as the best global partners. Moreover, by going beyond the threshold representing a turnover of 1 billion and more than 350,000 customers (many of them from Romania, as well), Veeam has crossed over into a new league so we expected that the event would be bigger, which actually happened.
We'll get back to the latest technologies released at VeeamOn 2019 and, anyway, this information can be found on the VeeamON official website. We'd like to shed some light on a few major directions in which the market is heading and which will affect, in various ways, our IT strategy, choices and budgets in the following years.
-
Data thefts and cyber attacks are 4th and 5th in the ranking of risks, according to World Economic Forum - Global Risks Report 2019. The first three positions are occupied by various natural disasters and climate changes, and weapons of mass destruction have already become a negligible risk.
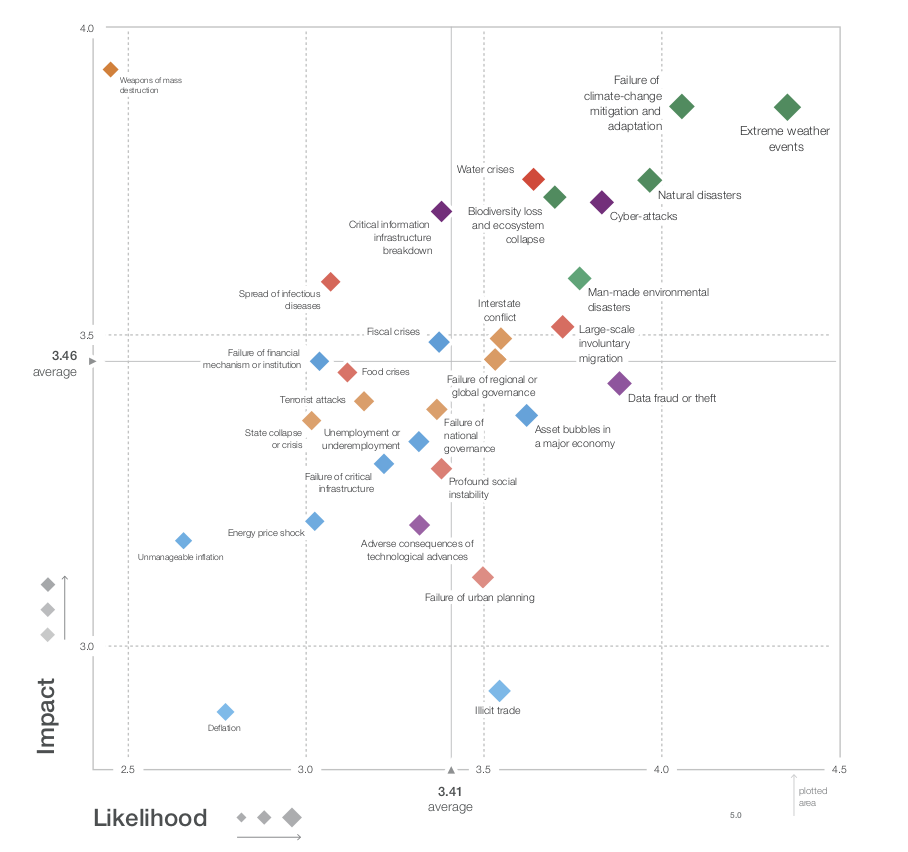
The direction is predictable and somewhat highlighted by news headlines, which show that the increasing incidence of cyber attacks is affecting millions of people, companies and organisations, at a rate that can become discouraging. On the other hand, the stakes of such attacks are mostly the theft of information, which thus becomes the most plausible risk associated with technology and digitalisation. The surveys conducted by the Global Economic Forum show that 82% of the participants expect an increase in the cyber incidents aimed at stealing money or information, and 80% of them consider that the next target is disrupting the operational systems.
Modern companies need Cloud Data Management. Backup remains a critical operation, however, more and more customers are building cloud infrastructures, which combine services from big service providers like AWS, Azure, IBM or Google and need more than backup. Both the escalation of cyber security incidents, and the multicloud approach require the harmonisation of several technologies to ensure data availability, which backup itself cannot cover completely. IT integrators must have new abilities and integrate solutions for backup on premises and cloud, data management and data governance, cloud migration and cloud mobility, security and access in order to successfully meet such requirements.
Hybrid cloud/on-premises approach brings benefits, but it also causes complications and additional risks due to the distributed approach and the high level of complexity. 73% of Veeam's customers have a hybrid cloud strategy, and this reality brings challenges for users (switching to new applications and services, lack of competences, resistance to change), for products (rigidity, integration difficulties, proprietary or legacy technologies), and for business processes (redesign, ensuring compliance, responsibilities). Thus, the services of a specialised IT service provider become all the more necessary.
Data dependency is critical, and Business Continuity and Disaster Recovery policies should cover any application, not just core business applications. According to the data presented by Veeam, 80% of the companies have recorded data-related incidents in the past two years, which needed a Disaster Recovery (DR) plan. On the other hand, only enterprise companies can afford a coherent operational continuity plan, although data dependency is widespread. Furthermore, the existence of a DR plan doesn't mean that problems are solved. Companies have to be able to constantly test and verify the functionality of such a plan, from user and application access to backup restore. This verification must be automatic in order to reduce costs, as well as the pressure on IT teams.
A new strategy is needed to ensure data availability and to cover as many risks as possible. This new strategy has five levels and covers the most diverse scenarios and business activities.
- Level #1: Snapshot of the main production systems, at intervals that are as short as possible (~1 hour), kept for a short period of time (~1 day). This will ensure a good level of protection against ransomware attacks.
- Level #2: Complete backup of all systems, at short intervals (~24 hours), kept for an average period of time (~14 days). Protection against a wider range of risks/attacks.
- Level #3: Secondary backup copy for all systems, every 24 hours, kept for 30 days in a secondary location. Protection against local disasters.
- Level #4: Backup to tape. For all systems, every 24 hours, kept for 1 year or longer, on-site or off-site. Protection against any disaster, long-term archiving, requirements of compliance with certain regulations, protection against ransomware attacks targeting backups.
- Level #5: Backup testing for all systems, automatically, every 24 hours. This ensures continuous backup validation.
For more information about complete backup strategies or Veeam solutions, do not hesitate to contact us!
